Anti-Phishing Software: The 4 Features You Shouldn’t Overlook
Adrien Gendre
—September 14, 2023
—4 min read

Phishing is one of the most common and costly types of cyberattacks—before and after an initial compromise. According to IBM’s Cost of a Data Breach Report 2023, the attack method is responsible for 16% of data breaches. And the threat shows no signs of diminishing for victims. In 2021 and 2022, Vade detected more than 1 billion phishing emails annually, a dramatic increase from volumes in 2019 (310 million) and 2020 (283 million). That explains the importance of email security solutions that include anti-phishing software.
In this post, we explore the topic of anti-phishing software and the four features you need to stay protected.
What is anti-phishing software?
As the name suggests, anti-phishing software is designed to neutralize phishing attacks. We can categorize anti-phishing software into three camps. First are the native security features provided by productivity suites like Microsoft 365. These provide valuable protections against phishing threats, but fall short in defending against advanced, dynamic, and unknown threats.
Second are secure email gateways, which have become less popular in recent years because of their limitations in terms of security and usability. SEGs don’t protect against insider attacks, require an MX record change that is visible to hackers, and don’t supplement native security tools. They’re also complex and time-consuming to deploy and configure.
Third are integrated email security solutions offered by third-party vendors. Given the limitations of options #1 and #2, Gartner recommends this solution to protect against email threats. It complements the native features of Microsoft 365, while offering enhanced measures for defending against today’s most advanced attacks.
Still, like any technology product, the efficacy of email security and anti-phishing software varies significantly among vendors. For optimal protection, you need anti-phishing software with four important features.
1. Advanced phishing and malware detection
Detection is your first layer of defense against phishing and clone phishing threats. It prevents emails with malicious links, files, or attachments from reaching users. Because most phishing threats remain undiscovered in the wild, anti-phishing software should provide the capability to filter unknown threats. This requires solutions that go beyond reputation- and signature-based detection to perform a behavioral analysis of email features and webpages. Unlike the former, the latter detects the anomalies present in all email-based attacks.
When evaluating solutions, consider three features which are needed for advanced detection. First, look for solutions that leverage AI models capable of filtering dynamic image- and text-based threats. Namely, this includes Machine Learning, Natural Language Processing, and Computer Vision algorithms, which together protect against every kind of phishing threat and evasion technique.
Second, consider the scale and quality of the dataset feeding the AI engine. The more current, relevant, and statistically significant the dataset, the more effective your detection capabilities.
Third, look for partners that are actively engaged in research and considered experts in email security. This often indicates their commitment to product innovations and improvements that can help protect you against the latest threats and techniques.
For example, Vade for M365 offers advanced threat detection that leverages a sophisticated AI engine. The engine combines Machine Learning, NLP, and Computer Vision models to learn from email intelligence gathered from 1.4 billion protected mailboxes.
Vade is also committed to ongoing research, a reason our solution is trusted by some of the world’s largest internet service providers (ISPs). In addition to continually adding new AI patents to our portfolio, we actively publish insights on the latest phishing threats and trends, including our quarterly phishing and malware report and annual Phishers’ Favorites eBook.

2. AI- and human-powered incident response
The discipline of cybersecurity isn’t perfect, which explains the need for incident response. This essential security layer enables you to identify and neutralize attacks that bypass initial detection. While many vendors often pay less attention to incident response than threat detection, the former is arguably more important. That’s because it enables you to protect against some of the most advanced threats at a time when you’re most vulnerable to exploitation.
Effective incident response requires both visibility and capability. Look for solutions that enable you to visualize your entire attack surface from one interface. This ensures you can identify threats with ease and address them without delay. Also, look for capabilities that allow you to remediate threats in bulk. You should also consider whether solutions allow you to create and set customizable alerts. Alerts ensure you stay informed in real-time, which can help you stop a potential data breach.
Vade for M365 empowers businesses with robust incident response tools and capabilities. Using the solution, you can view and address potential threats and user reports across tenants. Additionally, the solution offers Auto-Remediate, which automatically removes threats post-delivery based on the latest threat intelligence. And with Vade for M365, you can create and set personalized alerts to never miss out on timely intelligence.
[Related content] Why Users Should Report Suspicious Emails, and How to Manage Them When They Do
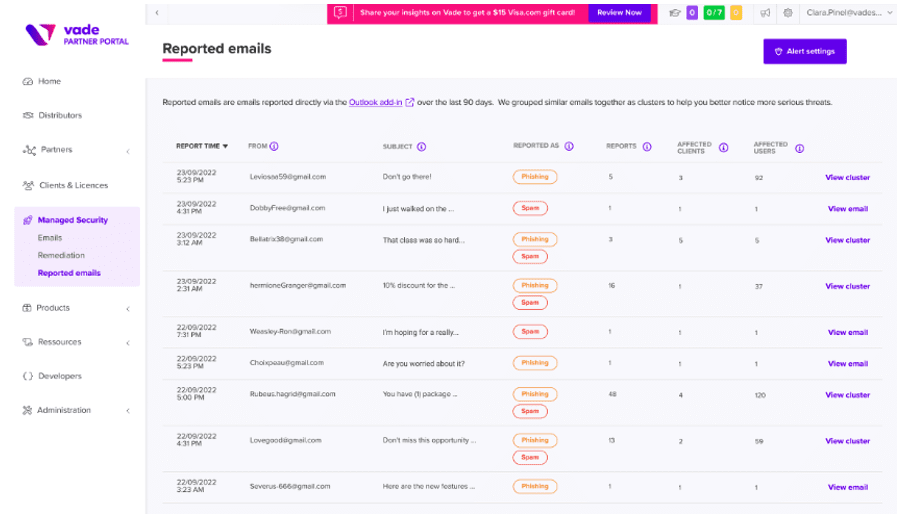 Reported emails dashboard in Vade for M365
Reported emails dashboard in Vade for M365
3. Threat intel and investigation tools
Investigating threats and gathering intelligence is a vital activity for strengthening your cybersecurity. That’s especially true when it comes to email, which remains the top attack vector. Email logs provide valuable intel that you can use to address current and future threats, as well as educate clients. Meanwhile, integrating your email intelligence with other cybersecurity tools can fortify your protections across your entire cybersecurity stack.
[Related content] 4 Vade for M365 Features That Help MSPs Sell Email Security
For optimal threat intel and investigation capabilities, look for solutions that integrate email intelligence with other security tools in your stack. This enables you to cross-reference intelligence and coordinate any response activities. Also, consider if solutions allow you to safely review and analyze the features of potentially malicious files and attachments. If they do, you can gather important evidence without risk of exposure.
Vade for M365 injects live email logs into any SIEM, SOAR, and XDR to communicate real-time email intelligence across your stack. Each email log contains valuable forensic information, including Microsoft’s verdict of the email and whether it passed DMARC, DKIM, and SPF protocols. File Inspector also enables you to safely analyze files and attachments contained in the email without risk to your admins.
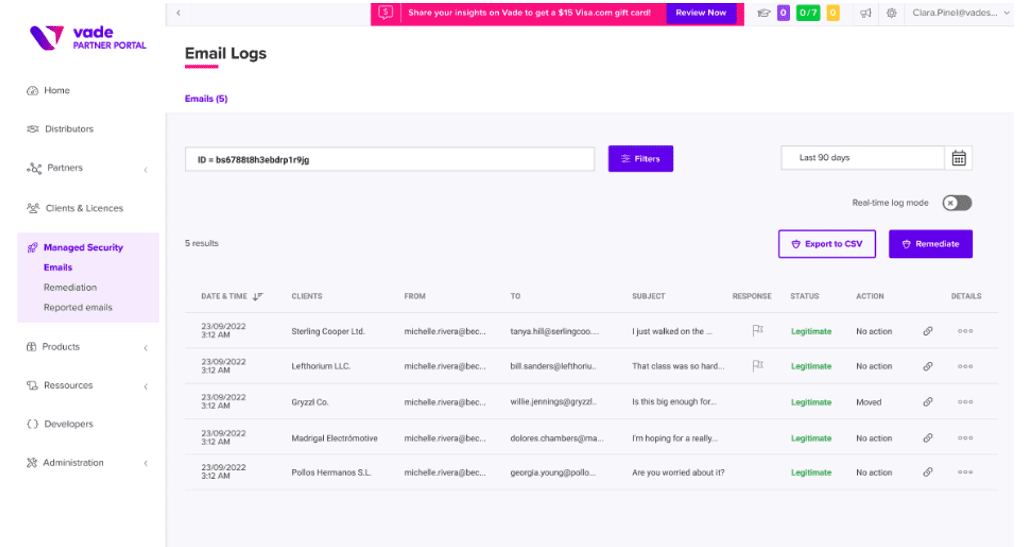
Email logs screen in Vade for M365
4. User awareness training and reporting
Users are the weakest link when it comes to your attack surface. Yet with the right tools and support, they can become a strength in your overall security posture. Security awareness training makes users proficient at identifying and remediating potential threats that could otherwise compromise your organization.
At the same time, the ability to report suspicious threats enables users to reinforce their learning and become active participants in strengthening your cybersecurity.
For optimal protection, consider if the anti-phishing software offers phishing awareness training. If it does, ask if the training is personalized, automated, and timely. Personalized means it accounts for each user’s context and email interactions. Training should also be administered at the time of need rather than according to a preset schedule. Timely education increases users’ ability to retain instruction.
[Related content] How Vade Delivers Phishing Awareness Training When Users Need it Most
Additionally, look for solutions that give users the ability to quickly report suspicious emails, and admins the ability to efficiently triage and remediate them.
Vade Threat Coach™ provides on-the-fly training to users whenever they encounter a phishing threat. The training is personalized to each user and reflects the brands they regularly interact with through email.
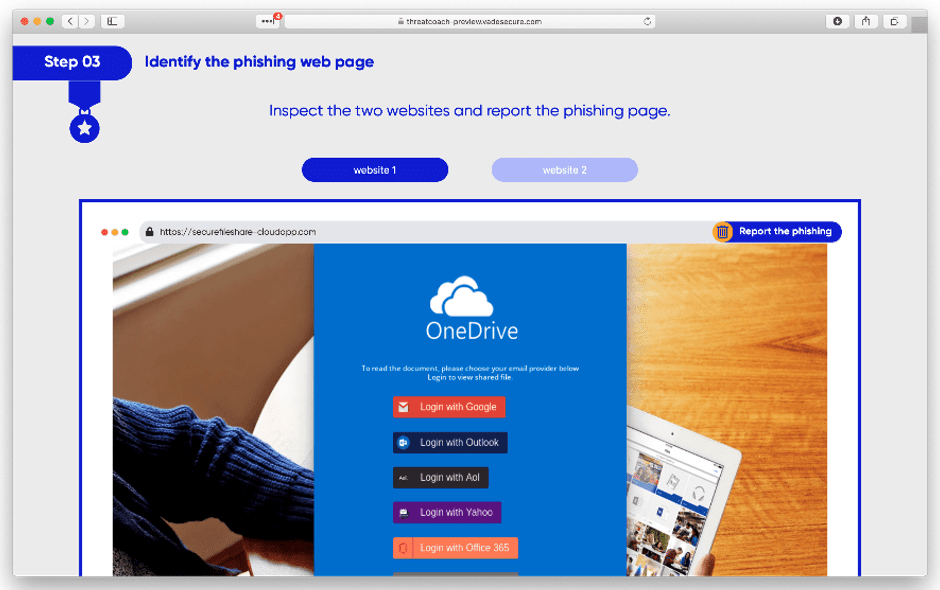
Real phishing page in Threat Coach™
Stay protected with anti-phishing software
As you read this post, hackers are engineering phishing campaigns to compromise your business. The threat landscape is unrelenting and unforgiving. To stay protected, invest in anti-phishing software that can offer you protection and peace of mind.
To test drive Vade for M365, take a self-guided, interactive tour.






