New Spear Phishing and Potential SIM Swapping Attack
Vade Experts
—January 24, 2024
—3 min read

Vade has detected a spear phishing attack that solicits phone numbers from intended victims. The targeted attack uses email spoofing and social engineering techniques to potentially facilitate SIM swapping or multifactor authentication (MFA) bypass.
In this post, we examine the details of the attack and what it could mean for your business, as well as present tips to stay protected.
New spear phishing attack solicits victim’s phone number
Vade detected a spear phishing attack targeting a single employee of a commercial real estate company.
The attack begins with an email that contains the attention-grabbing subject line, “FAST ONE!!!” Sent to the victim’s corporate email address, the message uses display name spoofing to impersonate an individual likely known by the victim. The domain name belongs to a randomly chosen Gmail account, which may be compromised.
The email explicitly references the victim and sender’s attendance at a business conference, suggesting the attacker has conducted extensive research on their target and the impersonated individual.
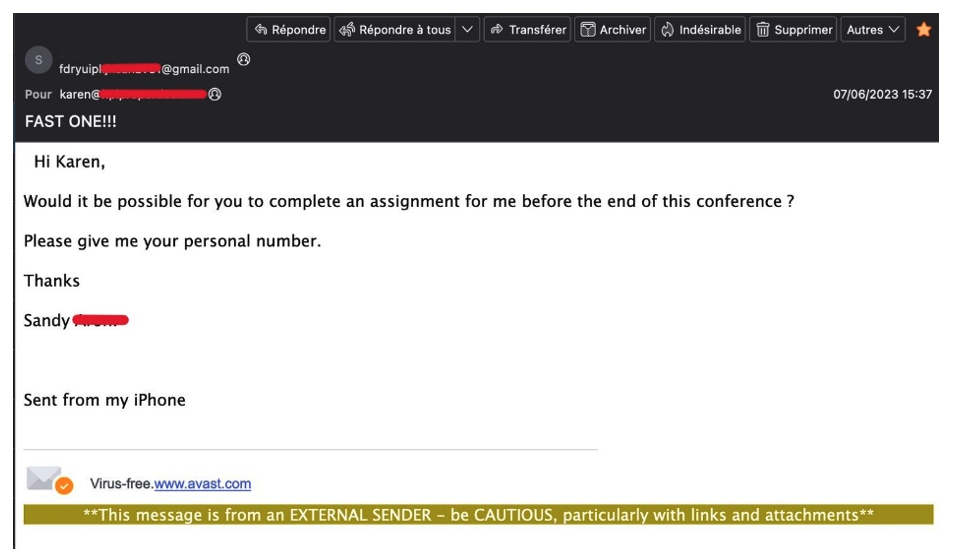 SIM-swapping - Spear phishing email detected by Vade
SIM-swapping - Spear phishing email detected by Vade
In the body of the email, the sender alerts the recipient that they need help completing an assignment before the end of the conference. They then include a request for the victim’s phone number. From the message, we can infer that the impersonated user and the intended target are likely colleagues, adding legitimacy and urgency to the request.
At the bottom of the message, the email contains the mobile signature, “Sent from my iPhone.” The added touch supports the illusion the sender is out of the office. It would also explain the request for a phone number and any subsequent text message the hacker might send.
While the request may seem harmless, it exposes the victim to significant risk if they comply. The technique (pretexting) can lay the foundation for smishing (phishing via SMS), which hackers use to harvest sensitive information or infect the victim’s device with malware. Smishing can also facilitate the acquisition of authentication codes needed for a multifactor authentication (MFA) bypass, a popular aim of man-in-the-middle (MitM) attacks.
Additionally, the hacker’s request can create the conditions for SIM swapping—an attack in which hackers transfer a victim’s phone number to a new SIM card in their possession. This gives hackers exclusive access to incoming calls and texts sent to the victim’s number, including authentication codes, passwords, and other important information. To facilitate SIM swapping, hackers often impersonate the victim, contact their wireless phone carrier, and convince the company to transfer the target’s phone number to a new SIM.
Why is this attack important?
The attack warrants attention for several reasons. For one, spear phishing continues to gain popularity among hackers as one of the most effective and lucrative attack methods. The threat lacks the characteristics security solutions depend on to identify attacks (malicious links or attachments). Rather, it uses social engineering tactics that are subtle and designed to create a convincing and realistic scenario in which victims take a compromising action.
The attack also targets the victim’s smartphone—a device that most users rely on to manage their digital lives—both personally and professionally. That includes communication, banking, security, digital storage, entertainment, and more.
Smartphones also present significant security vulnerabilities, as evident by numerous high-profile examples. The prolific cyber group Lapsus$ is infamous for using social engineering techniques and SIM swapping to facilitate data breaches. In 2022, the cyber group successfully breached Uber, Microsoft, Cisco, and other global brands.
These attacks prompted the US Department of Homeland Security (DHS) to launch an analysis of Lapsus$’s techniques, including SIM-swapping. Late last year, DHS’s Cyber Safety Review Board (CSRB) issued a report outlining recommendations to stop future attacks.
Following the report, the US Federal Communications Commission (FCC) recently announced new requirements for wireless phone carriers. Beginning July 2024, the companies will need to take additional measures to authenticate the identity of customers prior to transferring a SIM. The new rules intend to make it more difficult for hackers to facilitate SIM-swapping attacks by tricking telecommunications providers.
How to protect your business from spear phishing attacks
Protecting against attacks like this one calls for a combination of technological and human measures. Encourage users and clients to practice vigilance when receiving emails requesting personal information. This includes checking emails for the signs of spoofing, never implicitly trusting an email sender, and using an alternative communication channel to verify the authenticity of requests before sharing personal information.
From a technical standpoint, consider adopting an integrated email security solution that supplements the protection of cloud email platforms. Look for solutions that provide protection against spear-phishing attacks and can detect text-based social engineering attempts.







