BEC Attack Prevention: How to Protect Your Business
Adrien Gendre
—August 31, 2023
—4 min read

When it comes to cyberthreats targeting your business, few are more costly and menacing than business email compromise (BEC). Victims’ reported losses from BEC attacks totaled an eye-catching $2.7 billion in 2022. And that was only for scams reported globally to the Federal Bureau of Investigation (FBI). Verizon’s Data Breach Investigations Report 2023 found that BEC scams have nearly doubled in the past year alone.
Difficult to detect and designed to prey on the greatest weakness in your attack surface (human error), BEC threats pose a persistent headache to businesses of all sizes.
In this post, we examine the menace of the BEC attack and how your business can protect against this threat.
What is a BEC attack?
BEC, also known as spear phishing, is an email-based threat that impersonates an individual known to the victim. A BEC attack attempts to manipulate the victim into taking a compromising action that often leads to a financial reward for the hacker.
Unlike phishing scams, BEC attacks don’t contain malicious links, files, or attachments. Instead, the threat comes from hackers’ research of the victim and a set of social engineering techniques we review in this post.
[Related Post] BEC Scam: How to Avoid Becoming a Victim
There are several types of BEC attacks, each targeting specific roles within an organization. They include:
- CEO fraud: Threat actors impersonate a CEO or senior executive and target employees. Making demands and often requesting secrecy, CEO fraud can coerce employees into wiring large sums of money into fraudulent accounts or carrying out other actions, usually financially motivated.
- Tax fraud (also known as W2 fraud): Attackers impersonate an employee and request tax forms containing sensitive information from someone working in Human Resources.
- Payroll fraud: Hackers impersonate an employee and notify representatives in HR or accounting of changes to the employee’s banking information. They request future direct deposits to be sent to a new account, which is fraudulent.
- Lawyer fraud: Cybercriminals spoof attorneys or law firm representatives. They manipulate victims into paying fraudulent invoices or wiring funds to illegitimate accounts.
- Gift-card fraud: Threat actors impersonate a colleague or superior and request other employees to purchase gift cards on their behalf. Cybercriminals often request photos of the back of gift cards, rather than the cards themselves.
- Vendor email compromise: Attackers compromise a vendor’s account and use it to target clients, in many cases requesting the payment of invoices.
While these types of BEC attacks represent the most common variety, other forms of BEC are emerging. For example, the IC3 reported that hackers are targeting victims’ cryptocurrency accounts by impersonating members from financial institutions.
What techniques are used in BEC attacks?
Since they don’t use malicious links or attachments, BEC attacks depend on several techniques to compromise victims. They include:
- Email spoofing: Impersonation is a key element of BEC schemes. To impersonate a known individual, hackers use email spoofing, including display name, close cousin, or domain spoofing. Thanks to authentication protocols like Domain-based Message Authentication, Reporting and Conformance (DMARC), domain name spoofing is less commonly used in attacks.
- Pretexting: A form of social engineering, pretexting is often used in BEC schemes. Using extensive research on their target, hackers present a convincing case for carrying out a compromising action that victims may perceive as legitimate.
BEC attack prevention: how do you protect your business?
Below are several measures you can take to safeguard against BEC threats.
1. Email threat detection and remediation.
Email security solutions are the first line of defense against BEC attacks. These solutions can catch and filter threats, automate and assist with remediation, and enable timely and precise incident response.
For adequate protection, look for solutions that leverage Natural Language Processing (NLP) algorithms, which can detect text-based threats, such as pretexting, flag words, or language that conveys a sense of urgency. Keep in mind that NLP models require a large and current dataset to be effective. That’s why you should ask your email security provider about how many mailboxes they protect.
And because no cybersecurity solution can detect 100% of threats, you should also look for solutions that make it easy to investigate potential threats and respond quickly and precisely to security incidents.
Vade for M365 protects against BEC attacks. The solution leverages NLP algorithms that learn from more than 1.4 billion protected mailboxes. It also automates remediation post-delivery and enables admins to remediate threats across tenants in just a few clicks.
2. User awareness training
Security awareness training provides an added layer of security against BEC threats. These programs educate employees on the types of BEC threats they may encounter. Because threats target specific users, look for user awareness training that personalizes training to account for each user’s professional context. Also, focus on solutions that automatically administer education at the time of need, such as when users encounter a real threat.
3. User reporting
The ability for users to report suspicious threats offers significant value to your organization. It reinforces user awareness training, while also creating an added source of threat intelligence to improve incident response. Yet to work effectively, solutions need to make reporting efficient for users to report and admins to remediate.
[Related Post] Why Users Should Report Suspicious Emails, and How to Manage Them When They Do
Vade for M365 compiles and organizes users reports in a single pane of glass, where MSPs can remediate reported threats across tenants.
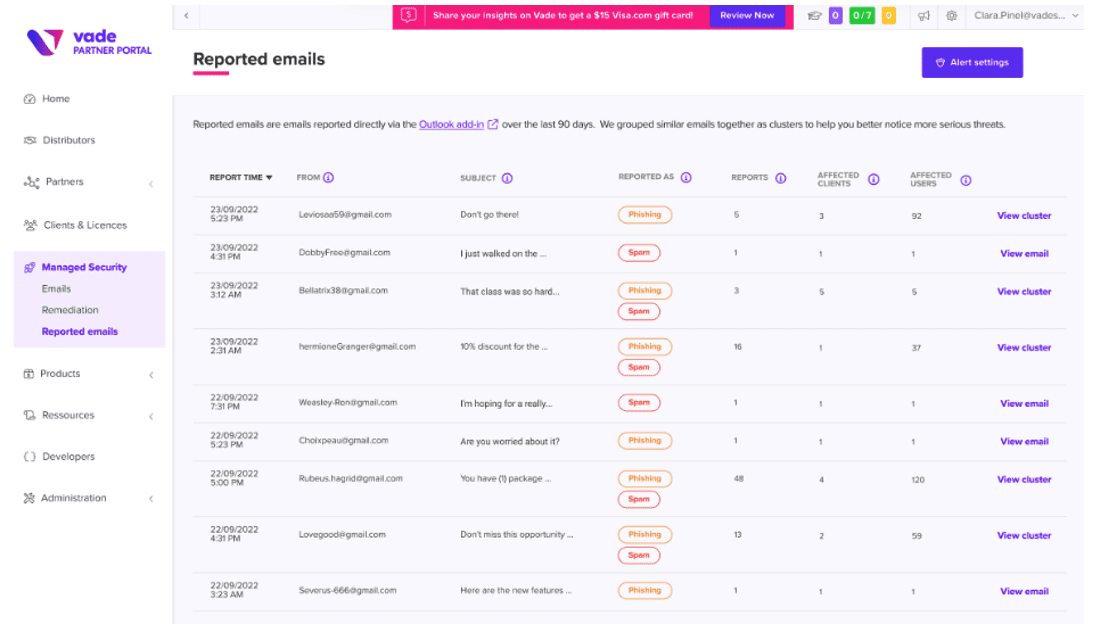
Reported emails dashboard in Vade Partner Portal
4. Threat reporting
The types and volume of BEC threats may vary by organization. That’s why you need reporting capabilities that provide you with insight into the BEC threats targeting your organization or clients.
Vade for M365 provides you with an on-demand report that details filtered BEC threats and classifies them by type, enabling you to understand the unique threat landscape for your organization or clients. For example, you can see how many instances of CEO fraud targeted your company compared to payroll fraud.
How Vade can protect you from BEC attacks
Vade for M365 is an AI- and human-powered email security solution that provides protection against BEC attacks, as well as phishing and malware/ransomware threats.
Integrated with Microsoft 365, the solution provides MSPs and SMBs with a low-touch solution that includes advanced detection, incident response, and threat intel and investigation capabilities. It also delivers automated user awareness training that is personalized and administered whenever users encounter a phishing threat.







