Clone Phishing: Protect Your Business from this Deceptive Cyberthreat
Adrien Gendre
—November 03, 2022
—5 min read

As a small-to-midsized business (SMB) or managed service provider (MSP), you fear this scenario. A clone phishing email exploits one of your employees, gives hackers access to your internal network, and opens the door for more ambitious attacks on your customers and partners. What begins with a moment of employee inattention or negligence quickly escalates into a devastating threat that jeopardizes your organization’s financial, operational, and reputational standing.
For many organizations, this scenario isn’t just a nightmare that keeps leaders awake at night, but an unfortunate reality. According to a study by IBM and Ponemon Institute, phishing cost businesses on average $4.91 million (USD) globally in 2021, representing the second most common cause of data breaches. In Q3 2022, Vade detected more than 203 million phishing emails, a more than 31% increase over the previous quarter. Contributing to the cost and scale of these attacks is the highly deceptive and effective subset of phishing called, “Clone phishing.”
If you run an SMB or MSP, clone phishing demands your time and attention. In this article, we examine the cyberthreat in detail, the common evasion techniques used to disguise it, and the solutions needed to effectively protect your organization.
What is clone phishing?
Imagine receiving a legitimate email from a brand you know and trust. Later you receive the same email again, only this time the sender explains they forgot to include additional recipients or information.
Without knowing the obvious signs of clone phishing, you trust the email as authentic and accept the sender’s reasoning without a second guess. After all, the email’s content and context give you no reason for suspicion. It turns out, however, that this second email isn’t legitimate, but a clone of the original message, intended to deceive you into clicking a malicious link or downloading a harmful attachment.
Clone phishing definition
Clone phishing is a subset of phishing that replicates a previously sent, legitimate email to exploit victims. Hackers intercept an email from a trusted sender, replace links or attachments with malicious content, and then resend the email to the same recipients. To avoid suspicion, hackers justify the purpose of the duplicate message with a simple and believable reason. They also use common phishing techniques to give the appearance of legitimacy, including spoofing display names.
Like common phishing schemes, hackers send the cloned email to a large group of recipients to increase the chances of compromising a user. In the event they secure a victim, they access that individual’s contacts and forward them the cloned email, spreading the reach of the initial attack.
Clone phishing is highly deceptive and devastating, especially to organizations like MSPs and SMBs. Once hackers penetrate the organization's internal network, they gain a foothold to launch spear-phishing campaigns, supply-chain attacks, and phishing schemes targeting other employees, customers, or partners.
Clone phishing attacks and techniques
Hackers use a variety of techniques to evade detection. This includes two types of email spoofing to make an email appear legitimate: Display name and close cousin spoofing. These two techniques are used most because they bypass DMARC technology.
Display name spoofing spoofs the sender’s display name but not their email address. In the below example, hackers send a phishing email impersonating Microsoft, with the display name reading “Microsoft Outlook” and the email address belonging to a Gmail account. For unsuspecting users, this discrepancy can be easy to overlook, especially when viewing the email on a mobile device, where most email clients only show the display name and hide the email address.
 Phishing email with display name spoofing
Phishing email with display name spoofing
With close cousin spoofing, the email domain name resembles the legitimate address but includes slight differences. These differences may be noticeable, such as a different domain extension, or undetectable to the human eye, such as Cyrillic characters that appear the same as those in the Latin-script alphabet. Below is an example of close cousin spoofing in which hackers use a different domain extension than the legitimate American Express website.
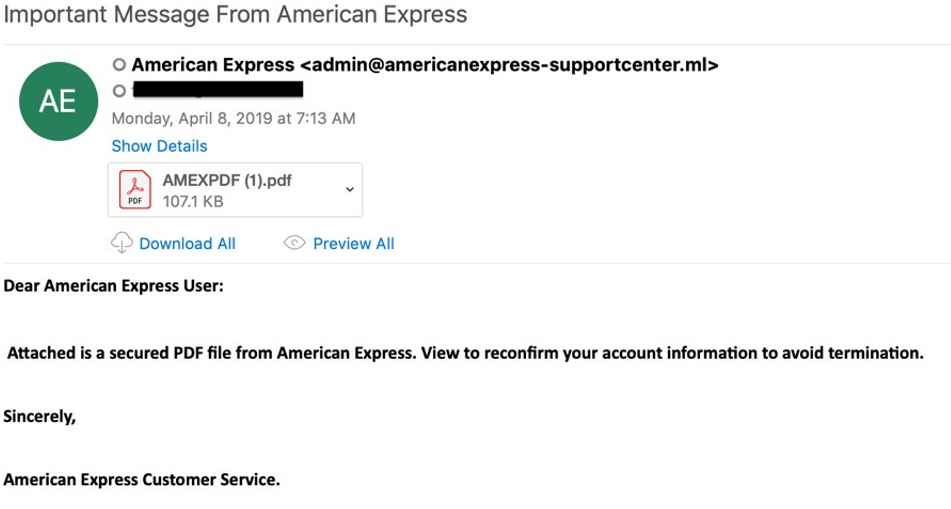 Phishing email with close cousin spoofing
Phishing email with close cousin spoofing
Another clone phishing attack technique is obfuscating URLs to evade detection by traditional email filters. Hackers may insert a legitimate URL into an email and redirect the link to point to a phishing page, a technique known as a URL redirect. Hackers may also disguise phishing links using URLs shorteners (e.g., bit.ly, Goo.gl, Ow.ly), conceal links in QR codes or attachments, or “stuff” emails with numerous legitimate links to trick filters into overlooking a single malicious URL, a technique known as URL stuffing.
The below example illustrates the URL stuffing technique. In addition to the malicious URL, the email contains multiple legitimate links to access Microsoft’s community, contact preferences, legal, and privacy webpages.
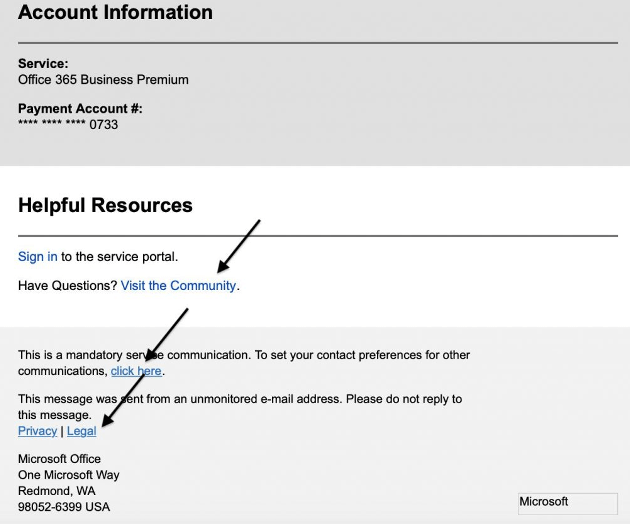 A phishing email with multiple legitimate URLs
A phishing email with multiple legitimate URLs
Clone phishing solutions
As with any cyber threat, protecting against clone phishing starts with embracing a comprehensive cybersecurity strategy. This includes both technology that can safeguard against modern threats and best practices that can transform your users from a cybersecurity weakness into a strength.
1. Adopt an anti-phishing solution
An anti-phishing solution is your first line of defense against a clone phishing attack. Anti-phishing solutions enable you to detect and respond to clone phishing in real time. For optimal security, look for solutions that leverage Artificial Intelligence (AI) to perform behavioral analysis of emails, URLs, and webpages. These solutions detect the anomalies present in all malicious content and filter both known and unknown threats. Traditional email filters, such as secure email gateways (SEGs), only defend against malicious content with known features such as specific malware signatures or blacklisted IP addresses.
For example, Vade for M365 uses a core set of AI technologies to perform behavioral analysis of emails, links, attachments, and webpages, including text- and image-based evaluation. Machine Learning algorithms scan 47 different features of emails and URLs, while Computer Vision analyzes images in emails and webpages to detect threats. Together, these technologies enable predictive defense against all incoming threats.
Additionally, you should look for anti-phishing solutions that provide threat response capabilities. Since no security solution can block 100% of threats, your solution should provide you with protection against threats that reach your users’ inbox and may move freely in your internal network.
For example, Vade's AI engine continues its threat detection analysis for emails post-delivery, automatically remediating threats based on the latest intelligence from more than 1.4 billion mailboxes worldwide. Vade also offers administrators the ability to track suspicious emails across their user base from a unified dashboard and remediate threats manually with a single click.
2. Invest in user awareness training
Users are often described as the weakest link in an organization’s cybersecurity posture. Yet with the right user awareness training, you can make them your greatest cybersecurity strength. When evaluating user awareness training programs, look for those that offer a personalized, timely, and relevant learning experience. These programs offer a superior alternative to classroom instruction or generic simulations by reflecting the content and context of users’ email interactions, and automatically delivering education on an ongoing, as-needed basis.
For example, Vade's Threat Coach™ provides on-the-fly, personalized user awareness training when employees need it most: when they encounter a phishing email. This contextually sensitive education reaches users when they’re most receptive to learning, increasing the likelihood they adopt and sustain the behaviors that strengthen cybersecurity.
3. Practice good cyber hygiene
Beyond technology and education, you should also encourage employees to adopt good cyber hygiene practices. This means being cautious when opening any email, recognizing that it can be spoofed. It also means carefully inspecting the email address of the sender and looking for mismatches between the domain and display names.
Your employees should also look for common signs of phishing, including spelling and grammatical errors, which are a common calling card of malicious foreign actors. For threats that evade human detection, consider also encouraging employees to use a URL analysis tool to inspect safely inspect suspicious links. For example, Vade offers IsItPhishing, a free tool that runs a real-time scan of URLs to determine if they’re malicious.
Clone phishing: Protect your clients and business
As an MSP or SMB, clone phishing doesn’t need to keep you awake at night. You can prevent it by investing in a strategy proven to upset cybercriminals’ nefarious plans and worst intentions. That calls for understanding the practice of clone phishing and institutionalizing the technology and practices to neutralize it.




