Microsoft Cybersecurity: Defending Your Top Vulnerability
Adrien Gendre
—April 27, 2023
—5 min read

Microsoft 365 is the world's most popular productivity suite with more than 345 million users. Yet its popularity has caught the attention of cybercriminals. The company is the most impersonated corporate brand in phishing attacks. Microsoft has also drawn continued criticism from the US government for inadequate cybersecurity and failing to meet basic security standards. The value it provides to users—ease of use, convenience, and efficiency—has opened door for new vulnerabilities in an organization’s attack surface. Businesses now find themselves in need of enhanced Microsoft cybersecurity, especially for email.
In this article, we examine two important ways cybercriminals are targeting Microsoft 365, and the four email security solutions you need to protect your business and clients.
Microsoft cybersecurity: the danger of email-borne threats
In 2022, Vade detected more than 22,500 unique phishing webpages impersonating Microsoft. The staggering total made Microsoft the most impersonated corporate brand—and #2 organization overall—in phishing attacks in 2022. Cybercriminals often send dozens, and sometimes hundreds or thousands of phishing emails containing the same unique phishing link, while a single domain can host thousands of phishing URLs.
If we look under the surface of this astonishing total, we find two important trends in how hackers are attempting to exploit Microsoft 365 and compromise more intended victims.
1. Hackers are exploiting new user behaviors
Productivity suites such as Microsoft 365 have changed how people use email. Today, individuals can now use an email message to directly open a document for editing, join an instant messaging feed, access large attachments, and more. As a result, many users treat email as the gateway to performing a variety of daily tasks.
And hackers appear to have taken notice. Vade continues to uncover phishing campaigns attempting to impersonate the integrations between Microsoft 365 applications. These campaigns often trick users into clicking malicious links that appear to be digital content embedded within the productivity suite, such as shared files or instant messaging feeds.

Phishing page impersonating OneDrive
2. Hackers are outsmarting traditional email security tools
Integration is an important value proposition of Microsoft 365. It's also a benefit that hackers are exploiting to create an appearance of legitimacy while evading detection by traditional email security tools.
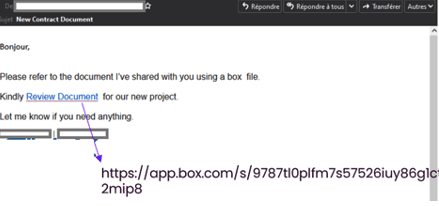
Phishing email exploiting Microsoft 365 integrations
In Q4 2022, Vade detected a phishing campaign that exploits Microsoft tools to disguise malicious webpages. The scheme sends a phishing email to users that contains a link to a productivity application.
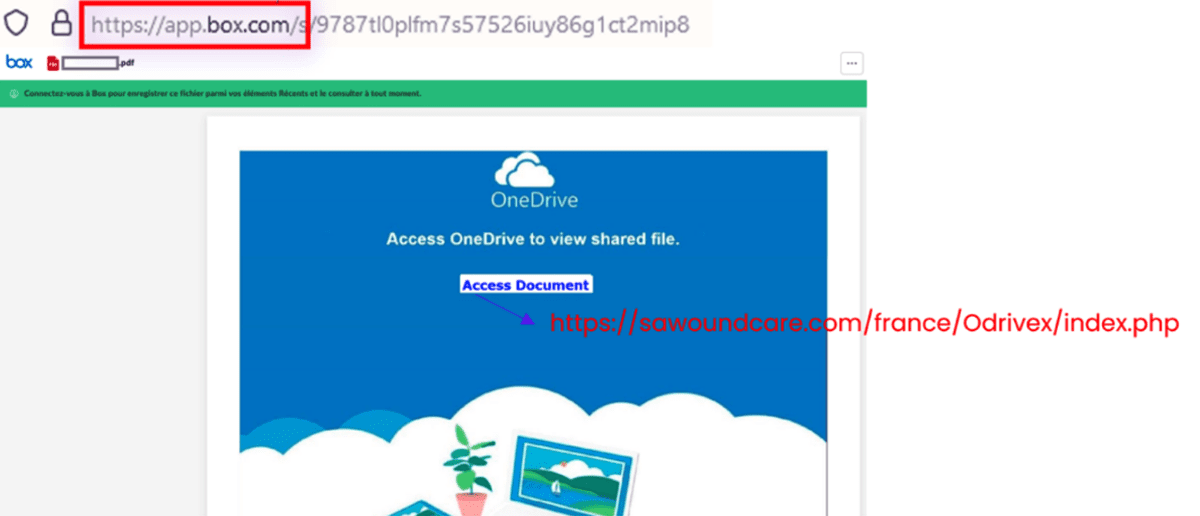
Intermediary page used in phishing attack
Once users click on the link, it directs them to an intermediary webpage that displays nothing more than a phishing link, which points to a destination phishing webpage. The final webpage contains fields for harvesting user credentials and gaining access to Microsoft 365.
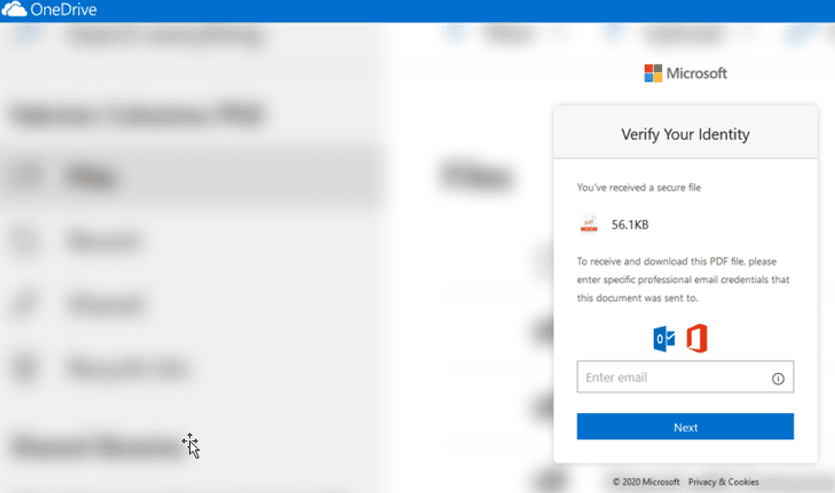
Destination phishing page
The attack is designed to trick email filters into scanning the intermediary page and marking the email as safe, without ever reaching the final phishing page. Without advanced email security, this phishing campaign can go undetected.
3. Hackers are carrying out multi-phased attacks
When a hacker compromises a Microsoft 365 account, the cybercriminal gains a foothold in your network to launch more targeted phishing campaigns and spear-phishing attacks.
This increases the need for solutions that not only safeguard email as the top attack vulnerability for network breaches but provides protections against the internal threats that may be transiting your networks.
How to enhance your Microsoft email security
Microsoft cybersecurity requires a comprehensive suite of advanced email security solutions designed to protect against the most dynamic zero-day threats. Here are four email security solutions you need for effective protection.
1. AI-powered detection and response
AI is seizing headlines for its strengths, weaknesses, and notable potential. Despite extensive media coverage, AI is often misunderstood. As a complex field and science, it isn't a silver bullet. In other words, AI solutions don't possess the same capabilities or provide equal value. They depend on several factors to work effectively and efficiently, including:
- Algorithms. In the world of email security, AI filters depend on algorithms to predict and catch cyberthreats. These algorithms come in different forms, which layer protections for specific kinds of cyberthreats.
For example, Computer Vision provides protection against image-based threats, such QR codes designed to disguise malicious links or distorted logos that have been altered to bypass detection. Natural Language Processing models detect the subtle grammatical construction, words, and phrasing that characterize spear-phishing attacks. Together, these models protect against all kinds of email-borne threats.
- Dataset. AI algorithms need data to learn. But not just any data. Instead, it needs a large, high-quality, representative, real-time, and continuous sample. The more that a dataset can fit this description, the more effective and accurate the AI algorithms can be.
- Human intelligence. AI depends on human intelligence. Data scientists are responsible for building the algorithms that power AI filters. Cybersecurity analysts are responsible for deciding which data to use to teach the algorithms so they limit bias and optimize accuracy. Users are necessary for providing new intelligence of emerging threats. Together, human intelligence—including its expertise and experience—help power AI.
2. Incident response capabilities
In cybersecurity, security incidents are inevitable. No solution can block 100% of cyberthreats, highlighting the need for capabilities that allow you to respond to incidents when they occur. Effective incident response solutions combine three important elements.
- Automated remediation. Human intervention is a limited resource constrained by time, personnel, and opportunity costs. To ensure optimal protection against threats that bypass initial detection, you need solutions that provide automated remediation based on new intelligence.
This remediation relies on the AI filter engine to neutralize threats based on new intelligence. To work, the AI engine must provide native protection and sit within your internal environment, rather than external to your perimeter.
- Manual remediation. Effective incident response also requires the ability for manual remediation, whether neutralizing threats or marking benign emails as safe. Because of your constraints on time and resources, you need solutions that automate duplicative tasks (such as remediating in bulk) and maximize efficiencies through smart features.
- Unified dashboard. When it comes to incident response, time matters, and so does visibility. Managed service providers (MSPs) need a unified, multi-tenant solution that allows them to access and manage their incident response from a single interface.
3. Threat intel and investigation
Your incident response depends largely on your threat intelligence and investigation activities. That's why you need solutions that support and enhance your ability to gather new intel, examine reported threats, and help you coordinate your evidence gathering.
Threat intelligence and investigation depends on three tools:
- File deconstruction. Safely downloading and examining potential email threats is especially important. This enables you to examine forensic evidence and use it to understand the potential spread of threats in your network. Look for solutions that enable you to inspect malicious emails and attachments without exposure to risk.
- User-reported emails. Without the proper tools, user reports can go unaddressed or overburden busy admins. For this reason, you need solutions that make it easy for users to report suspicious emails and for admins to review and remediate them. This calls for grouping similar reported emails together with those that are also similar, yet unreported.
- Integrations with SIEM, SOAR, XDR. Organizations rely on multiple cybersecurity tools, making the task of coordinating intelligence time-consuming and potentially compromising.
Because email is the top attack vector and the number one source of threat intelligence, you need solutions that integrate your email logs into any Security Information and Event Management (SIEM), Security Orchestration and Automated Response (SOAR), or Extended Detection and Response (XDR) system. This enables you to improve your intelligence gathering and response capabilities.
4. Phishing awareness training
The number one cause of data breaches is human error. Considering that human interaction with cyberattacks occurs mostly through email, it's no surprise that phishing awareness training is one of the most important solutions you can implement.
But like AI solutions, security awareness training programs don't provide the same value. Their effectiveness depends on three factors.
- Automation. Users need training that independent of human intervention. By automating training, you can ensure users get the training they need without adding to the responsibilities of busy admins.
- Personalization. Generic phishing templates separate training from lived experience, minimizing the value of applying learning in a real-world context. For this reason, users need phishing examples that mimic what each of them personally encounters every day.
- Continuity and timeliness. Training isn't an event, but an ongoing need as new threats surface and techniques challenge users' understanding of what constitutes a threat. That's why phishing awareness training should be delivered on as-needed basis, with need defined as the moment users encounter a phishing threat.
Microsoft cybersecurity: how to step up precautions
Microsoft 365 empowers your teams with new capabilities for communication and collaboration. Yet it also exposes you to risks that present lasting consequences for your business.
As the most targeted business application in the world, the question isn't if but when you'll encounter the next cyberthreat targeting Microsoft 365. That's why you should adopt the Microsoft cybersecurity solutions that can provide advanced and ongoing protection.
Vade for M365 is a collaborative email security solution for Microsoft 365 that combines AI and human expertise to catch the dynamic threats that Microsoft misses.




