Spear Phishing vs Phishing: What’s a Greater Threat for Your Business
Adrien Gendre
—September 07, 2023
—4 min read

Spear phishing, also known as business email compromise (BEC), was the costliest email threat in 2022, resulting in reported losses of more than $2.7 billion for victims. Meanwhile, email-based phishing produced the highest victim count of any cyberthreat, with more than 300,000 recorded over the same period. That raises an important question. When comparing spear phishing vs phishing, which is a greater threat for your business?
In this post, we examine the similarities and differences between both threats and present important measures to protect against them.
What is spear phishing?
Spear phishing is a targeted attack aimed at a limited set of potential victims. Highly effective, costly, and menacing, the threat impersonates an individual known to the victim—such as a colleague, boss, or acquaintance—and uses social engineering techniques to manipulate them into taking a compromising action.
There are several types of spear phishing attacks, which vary by tactic and often the professionals they target. Common types include CEO fraud, tax fraud (W2 fraud), gift-card fraud, lawyer fraud, and payroll fraud.
Spear phishing uses common evasion techniques to outsmart traditional email filters. They include:
- Email spoofing: Email spoofing impersonates the display name or domain name of a legitimate sender with an exact or close replica.
- Pretexting: A social engineering technique, pretexting attempts to earn a victim’s trust before making an eventual demand. Hackers use this technique to manipulate victims without using malicious links or attachments, which email filters can detect.
- Urgent demands: Like pretexting, hackers convey a sense of urgency to coerce victims into action.
- Mobile signatures: Another text-based technique, hackers add mobile signatures to create the illusion of being out of the office or country. A common deceit, this tactic helps explain the urgency of demands and any grammatical errors or misspellings. One example of a mobile signature is the phrase, “sent from my iPad, iPhone, or Android device.”
[Related post]: BEC Attack Prevention: How to Protect Your Business
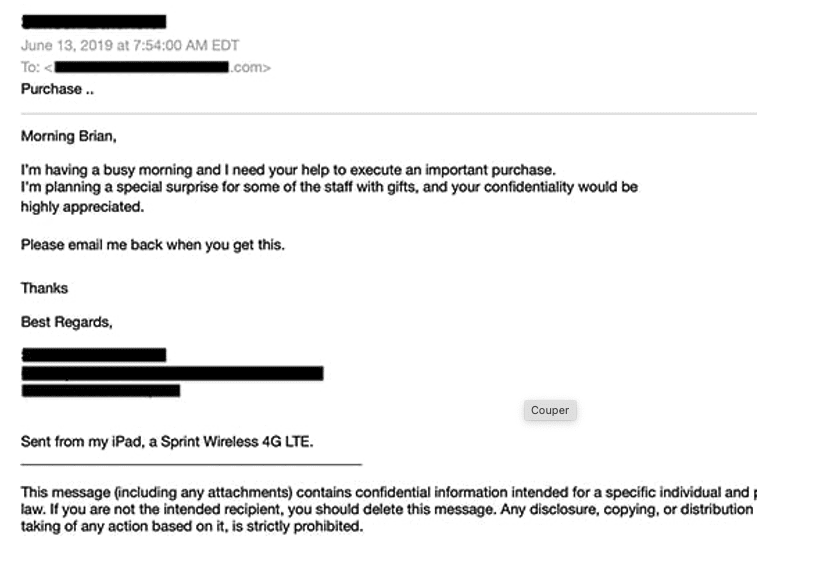
Spear phishing email detected by Vade
What is phishing?
Phishing is an email-based threat that impersonates established, well-known brands. Phishing threats distribute malicious links, files, or attachments to compromise victims. Traditionally, this attack variety has targeted large populations of victims indiscriminately.
More recently, however, phishing campaigns have become more targeted and personalized. Consider the example below of a campaign targeting Microsoft 365 users. The phishing email uses the victim’s email address in the subject line. It also directs them to a fake Microsoft 365 authentication page, which prepopulates with the victim’s email credentials.
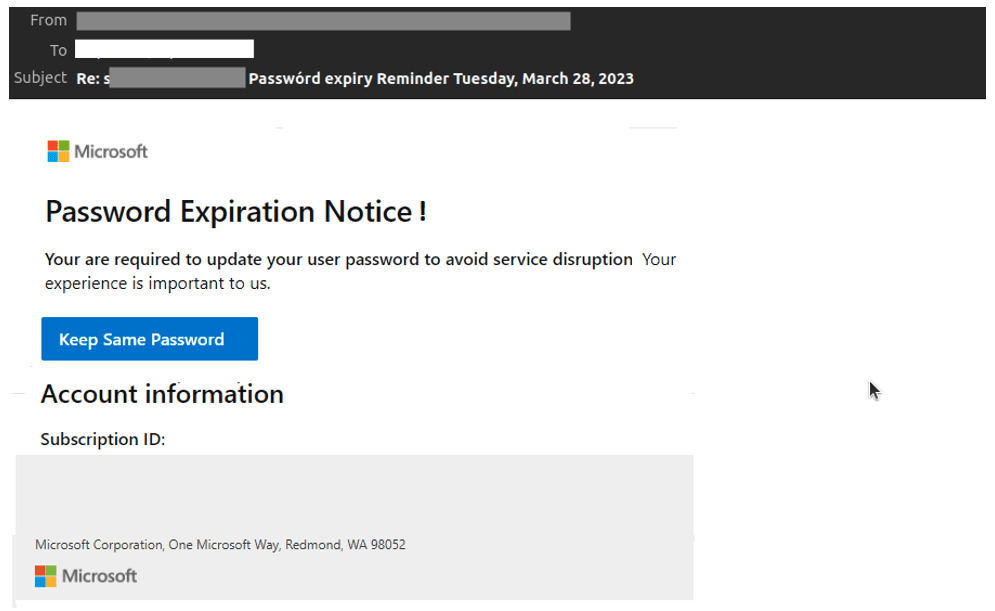
Microsoft 365 phishing email detected by Vade
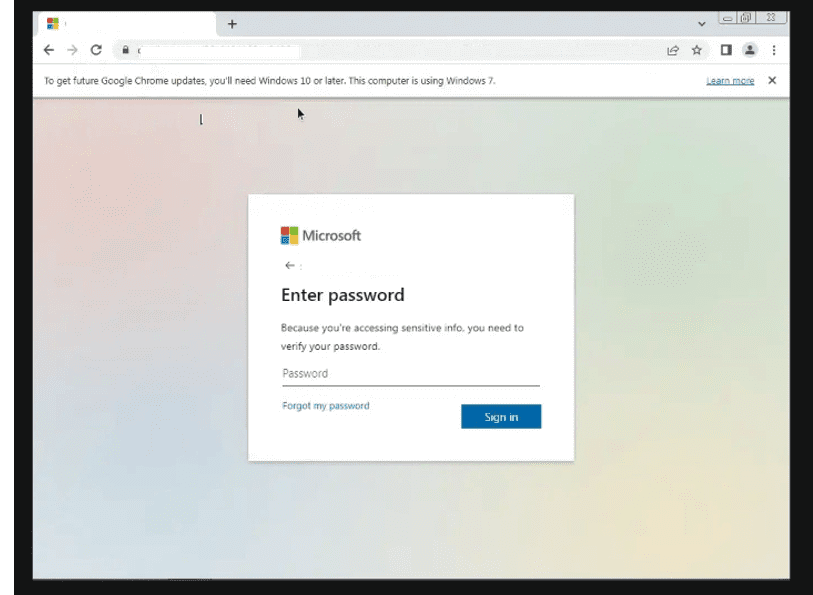
Microsoft 365 destination phishing page detected by Vade
Several trends help explain the trend toward targeted attacks. Thanks to phishing awareness training, users have become more proficient at spotting and reporting phishing threats. Also, phishing kits have automated the personalization of attacks, allowing hackers to launch targeted campaigns without extra time or effort.
[Related content]: H1 2023 Phishing and Malware Report: Phishing Threats Increase 54%
Phishing uses common evasion techniques to outsmart traditional email filters. They include:
- Email spoofing: Like spear phishing, phishing threats impersonate the display or domain names of legitimate senders.
- Image or logo manipulation: Hackers alter the signatures of brand logos or images to bypass traditional email filters.
- Obfuscating URLs: To bypass detection, phishing threats redirect URLs, use URL shorteners, conceal URLs in QR codes or attachments, or stuff legitimate URLs into malicious emails.
Phishing emails may direct users to a fraudulent website to harvest user credentials, while others may deliver malware—including ransomware—to infect systems. For ransomware attacks, email remains the primary means of distribution.
How is spear phishing different from phishing?
Spear phishing and phishing attacks share notable differences and similarities. They include:
- Techniques: Phishing emails use malicious links, files, or attachments to harvest credentials or infect systems with malware. Spear phishing emails use social engineering techniques and spoofing to compromise victims.
- Volume: Phishing is a high-volume threat compared to spear-phishing attacks. The IC3 received nearly 14 times more victim reports of phishing attacks than spear phishing in 2022.
- Success of compromise: Both phishing and spear phishing are effective threats. According to the IBM Cost of a Data Breach Report 2023, phishing accounted for the most data breaches at 16%, while BEC was responsible for 9%. Accounting for threat volumes, however, spear phishing compromises more victims on a per threat basis.
- Scope of target: Phishing often targets large populations, while spear phishing focuses on small cohorts. This is due to the entity being impersonated and the effort involved.
- Cost: Spear phishing and phishing attacks are most often financially motivated. However, there is a difference in cost per incident. Reported phishing losses totaled more than $52 million in 2022, a fraction of the more than $2.7 billion reported by BEC victims.
How do you protect against spear phishing vs phishing attacks?
Protecting against spear phishing attacks requires a unique set of solutions, many of which overlap with anti-phishing measures.
Spear phishing protection
Below are some of key anti-spear phishing measures:
- Natural Language Processing (NLP): Natural Language Processing (NLP) models provide special defense against spear-phishing attacks. Designed to understand human language, NLP can detect the text-based threats used to manipulate victims. This includes flag words, pretexting, and conveying a sense of urgency.
- Anomaly Detection: A subset of Machine Learning, Anomaly Detection can identify anomalies in an organization’s communication patterns and email traffic. It can also detect advanced spoofing techniques that can bypass authentication protocols, such as cousin domains and display name spoofing.
- Warning Banners: Customizable warning banners alert users of a potential threat without disrupting email flow.
Phishing protection
Below are also a few key anti-phishing measures:
- Computer Vision: Computer Vision algorithms detect image-based threats, including QR codes containing malicious links, text-based images, remotely hosted images, and altered brand logos.
- Mobile Rendering: Pages are explored across different device-browser combinations (e.g., Safari on iPhone, Chrome on Android, etc.) to thwart attacks designed to only display their content on mobile devices.
- Regional Page Exploration: Pages are explored from different regional zones—such as North America, South America, Europe, and Asia—to combat phishing pages that display their content only when accessed from the targeted location.
Spear phishing and phishing protection
Below are other important spear phishing and phishing measures:
- Machine Learning: Analyzes features of emails, URLs, and attachments to detect anomalies or malicious behaviors. Machine Learning algorithms train using massive data sets of malicious and benign emails to recognize features consistent with all cyberthreats.
- User awareness training and reporting: Security awareness training teaches users how to spot and handle threats in real-time. Meanwhile, user reporting capabilities enable them to report suspicious threats to admins for remediation.
- Incident response solutions: These features enable admins to triage and remediate active threats, including those reported by users.
How Vade can protect you from spear phishing and phishing threats
Vade for M365 is an AI- and human-powered email security solution that provides protection against phishing, spear phishing, and malware/ransomware attacks.
Integrated with Microsoft 365, the solution offers MSPs a low-touch solution that includes advanced detection, cross-tenant incident response, and threat intel and investigation capabilities. It also delivers automated phishing awareness training to users that is personalized and administered whenever they encounter a phishing threat.








